It all started with a confused email from the marketing team: “we’ve got an odd website which looks like iProperty Group asking users for their emails, can you help us take it down?”. I clicked on the link and, sure enough, there’s a site which claims to be ours and informs me that “to access our online secured properties auction page, you are required to choose your email address below”. Take a look, this is how it appears to a user:
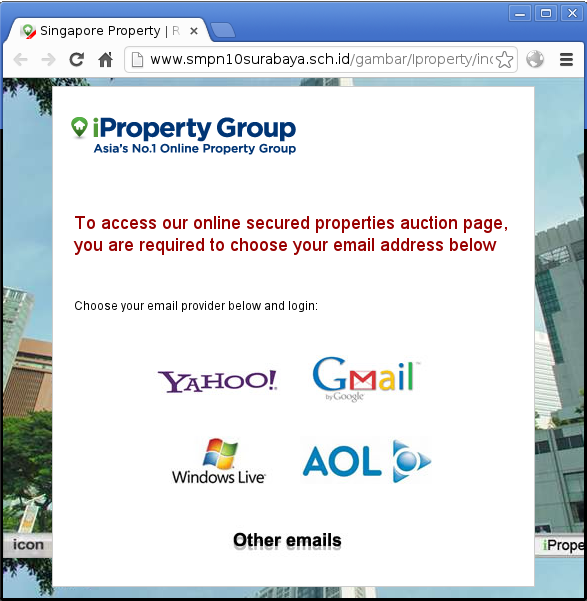
Being an experienced internet user and naturally suspicious, this screams scam to me - bad grammar, bad design, asking for your email password; surely no-one could be taken in and believe that the site was legit. Could they? Even so, I knew we had to get rid of it. And that’s there the adventure begins. You see, “take it down” seems like a pretty reasonable request. That is, until you’ve had to deal with over 40 of them in a week. We’ve put a script in place at the start of May which alerts us when one of these sites pops up - on average we’ve been seeing 6 to 8 new ones a day. Sometimes we see multiple URLs on the same domain but mostly we get brand new pages on a domain we’ve not dealt with before. And that means another round of finding the host and trying to get it taken down.
So far we’ve managed to get over 30 of them taken down; here’s what we’ve noticed:
Web hosts vary wildly but it can take days to get a page taken down
Time is of the essence when these pages go up. The scammer will usually upload to their chosen target site, test it to make sure they’ve installed it OK and then proceed to start emailing their victims. If we can get the page taken down before their first email is sent out then they’ve put in work to compromise a site without any payback. If we do this consistently then our hope is that they’ll give up and move on somewhere else.
Our team have been very dedicated in reporting pages as soon as we notice them. That usually involves sending an email to the abuse contact for the hosting company running the compromised site. We’ve had some great responses where the hosting company has responded to us within 45 minutes of the notification to let us know they’ve suspended the account or removed the content. However, more often than not we find ourselves following up multiple times and waiting days before the issue is resolved. Our current record is a site that’s been up for 4 days and is still live - I won’t name and shame the host… yet!
Contacting some web hosts is nigh on impossible
In the best case, when doing a whois on an IP we get an abuse@ email address at the hosting company, we email that address and get an autoresponder from a ticketing system and the issue is tackled in under 24 hours. However, that’s pretty rare - usually the email bounces or ends up in a seeming blackhole.
That’s when the fun detective work starts - how else can we get in touch with the site owner? Doing a Domain whois will sometimes give you a hit but often the email will also bounce or the domain record has been privacy protected. In some cases (.ca, I’m looking at you), there’s just no contact details to go off at all.
So if there’s no luck on the domain registrar records, it’s off to explore the compromised site to try and find a contact form, an email address, anything to identify someone in charge of the site. Of course, the problem now is that you’re either contacting a web designer who put the site up for a client 5 years ago or you’re scaring a small business owner by telling them their website is hosting a phishing page and they don’t have the faintest idea how to solve the problem.
Google are efficient at adding new sites to blacklist. Microsoft? Not so much
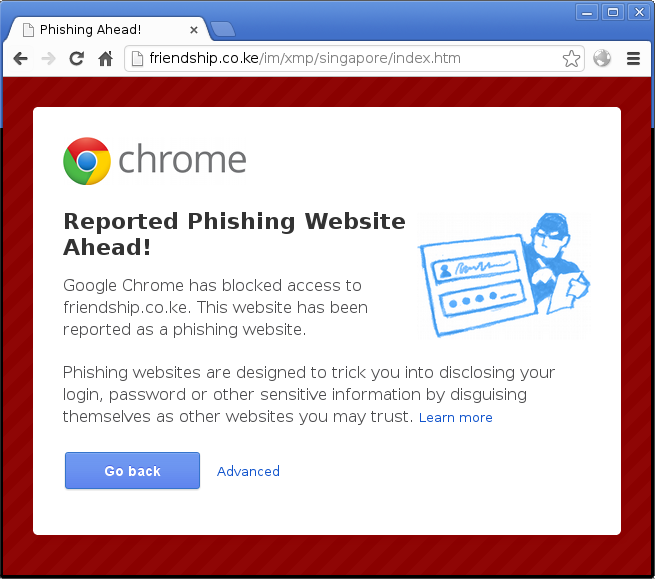
Although the ultimate goal is to get the page taken down, having it blacklisted by Google’s Safe Browse list and Microsoft’s SmartScreen is a good first step. We know that we can stop some people falling victim to the scam if they’re using a recent web browser. If the site is included in Google’s list, you’ll get a big warning page in Chrome:
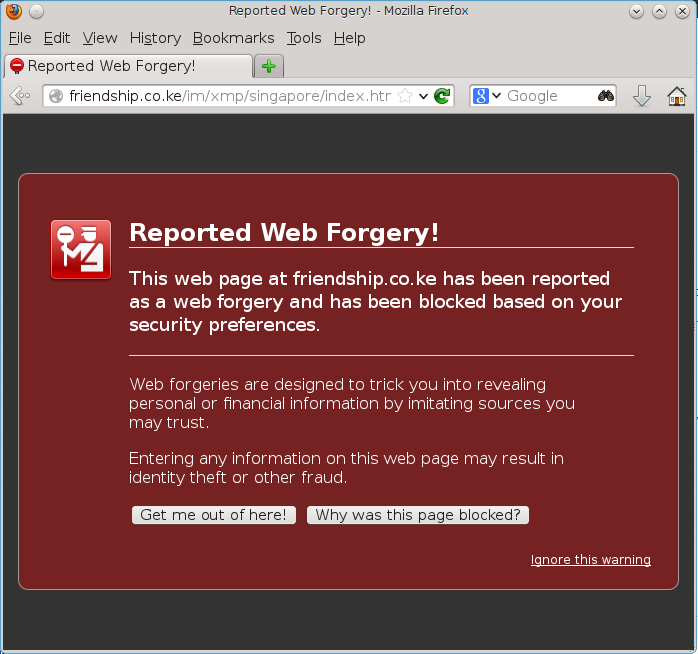
And Firefox:
And any email including the email will get flagged by Gmail:

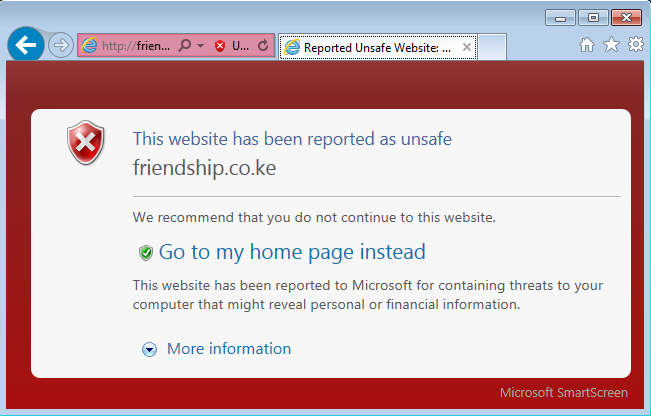
If the site is in Microsoft’s list, you’ll get a warning page from IE (from v8 onwards anyway):
However, getting onto Microsoft’s list is very hit and miss. From my experience, Google typically add new sites to their list in around 12 hours. Our experience with Microsoft has been that it can take upwards of 3 days to get a site blacklisted (by which time, hopefully, the site will be gone). Initially we also tried to submit pages to antivirus blacklists also (Symantec, TrendMicro, etc) but that was far too much work with minimal payback.
Today, Google Safe Browse is the closest we have to a universal list of suspicious websites (it’s supported by Chrome, Firefox and Safari). If Google were to donate the project to the W3C and it were adopted by more browsers it would be a net positive for the internet community.
Lots of people and companies have websites that they’ve not touched for a long long time
When exploring the compromised sites to try and discover contact details it’s immediately obvious that the site has not been maintained for a long time. It’s not just a case of running a vulnerable framework or software but sites which just don’t work and have probably been forgotten many years ago but someone, somewhere is still paying for it to be live.
WordPress and Zen Cart are the most common attacked platforms
We’ve also done some analysis on the sites that have been hosting phishing pages trying to determine how the site was compromised and if there’s any patterns. Unsurprisingly, almost all of the sites ran Apache (one site was running Nginx, one was running LiteSpeed) and all of the servers had PHP installed however those are not necessarily the attacked platforms. Of the sites which were compromised, over half were WordPress sites; the second most common software package running was Zen Cart.
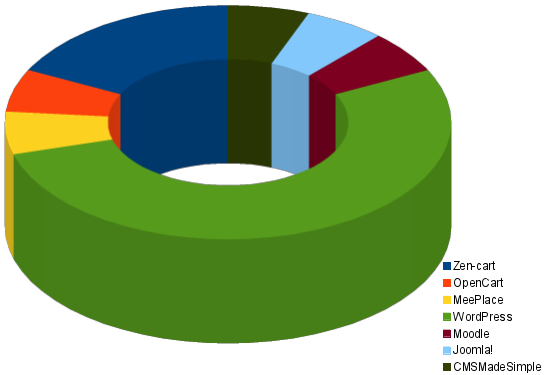
We also noticed some sites where the scammer had added a new DNS record to a domain in order to make the site seem more legitimate (e.g. “http://www.iproperty.sg.targetsite…”). In theses cases we can only guess that the attack vector was the web hosting control panel.
These scammers are very persistent
As I’ve noted before, we’ve been seeing 6 to 8 new sites a day just targeting iProperty Singapore. Our hope is that if we’re efficient enough in getting sites blacklisted and taken down that they’ll realise the effort of running the scam against us is more than the return they’re getting. However, we’ve also seen the same basic attack (same HTML, different images) targeting other sites such as gunsamerica.com, homes.com and vrbo.com.